.

.
.
Related Links
What is Multi-Factor Authentication
Multi-Factor Authentication not only requires a username and password, it also requires something you have or something you are. Impersonating a user without the device or biometric is not possible. Multi-factor devices include key chain tokens, voice or text phone messaging, USB devices, printed cipher grids, and biometric readers.
Security Credential Device These are usually small key-chain devices, which are the size of an automobile wireless remote. Some also come in a credit card sized form factor. They have a small LCD display that shows a number every few seconds or when a button is pressed. Some manufacturers also offer software based tokens, eliminating the key-chain device. Software devices are now common for many mobile phone models.




Voice/Text Message Companies such as Facebook and Google are offering this. When a user logs in, they enter their username and password. If these are valid, the system then sends a text or voice message to a predetermined phone number. The message contains a temporary "verification code". The user then enters the verification code in the next screen. If the code matches the one sent via text message, the user may access their account. For more details see < ahref="content.Healthy_Passwords_How_To_Setup_Google_2-Step_verification.html">Google's 2-step authentication setup and Facebook login notification setup instructions.
USB Devices  USB Devices are similar to key chain devices. Rather than displaying a value, they can work directly with the software when plugged in or they can have special software you run from the device. Like the first and second device, a user enters a username / password, and if they are correct, they insert their USB device. If it registers as the correct unit, access is granted. There are other variations to this where a user may put a special file on the USB device of their choosing. The system will then use it for future authentication.
USB Devices are similar to key chain devices. Rather than displaying a value, they can work directly with the software when plugged in or they can have special software you run from the device. Like the first and second device, a user enters a username / password, and if they are correct, they insert their USB device. If it registers as the correct unit, access is granted. There are other variations to this where a user may put a special file on the USB device of their choosing. The system will then use it for future authentication.
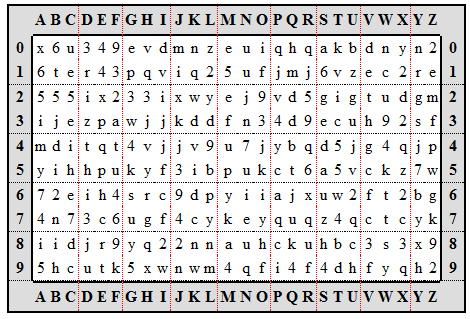
Cypher Matrix The issuing site provides a paper grid with different codes in a checkerboard sort of pattern. When you login, they ask for the codes in certain x/y coordinates. You use the grid to determine the verification code.
Biometric Readers These include finger-print readers, retinal scanners, and even algorithms that analyze your typing patterns. The current problem with biometrics is they require a layer of software on the operating system making roaming users a challenge.


|
Learn to Make Strong Memorable Passwords Today |

|
| ISBN: 978-0615456850 |
.
|
|
||
|
Home | Live CD Listing | Password Worksheet | Third Party Ratings | Purchase | Errata | Contact | News | News Archive | Legal Copyright © 2011, Sustainable Alternatives, LLC | Ligonier, PA 15658 | 724-238-9560 | All Rights Reserved. |

|
|
 |
.

