.

.
.
Ironkey S200 Review
Ken Klein, Healthy Passwords
June 8, 2011
Rating: 4 1/2 out of 5
The security industry has long considered Ironkey to be “the” premiere flash drive. We wondered how user-friendly Ironkey would be for non-technical users, so we decided to evaluate the drive from a non-technical perspective.
Ironkey Features
Military-grade Hardware Encryption.
Waterproof.
Support for Windows, Mac OS X, and Linux.
Portable Application Support (Apps living and running only on flash drive).
Identity Manager for Password Management. (Windows Only)
Verisign Identity Protection Built into Identity Manager. (Windows Only)
Secure Sessions Service to encrypt browser traffic. (Windows Only)
Self-Destruct after 10 consecutive invalid password attempts (just erases flash).
Online management account to backup Identity Manager records. (Windows Only)
Optional ability to reset hardware password online.

We tried the 2 Gigabyte S-200 unit. The 4 Gigabyte D-200 unit is almost the same price, but we decided to use the faster of the two technologies. The only difference between the D-200 and S-200 model is the case color and type of memory used. The S-200 uses something called SLC Flash, which is a little faster memory than the D-200, which uses something called MLC flash memory.
Summary
We rate the Ironkey 4 ½ out of 5. It loses a point for the password manager, but gains a half for the indestructible hardware.
From a Microsoft Windows user perspective, we love the Ironkey. It’s like buying a well built luxury car. It cost much more than the competition, but almost everything about it feels good. The one complaint we have is the Identity manager (Password Manager). Using our luxury car analogy, the Ironkey identity manager like having vinyl seats in a Lexus. Fortunately, there are other good password managers that can be stored on the Ironkey. One of the nicest features of the Ironkey is called secure sessions. If you use public hotspots, this can save the expense of a monthly VPN service fee.
From a Mac OS X user perspective, we like the Ironkey. The hardware is great. You still have the graphical control panel and online hardware reset, but you lose secure sessions, identity manager, Verisign VIP support and secure backup. If you are running on an Intel based Mac, windows emulation may enable this support. We will post a follow-up in the near future after testing this. As a Linux user, we still love the Ironkey. After all, linux users are like the muscle car users of the computing world, and what muscle car owner wouldn’t go for the IronKey hardware. Besides that, Linux users are innovators and tinkerers, and will probably get everything they want working through emulation.
Purchase
We ordered our evaluation unit from Amazon.com for 81.99 US Dollars. The item was available for Prime shipping, eliminating shipping charges. The unit arrived two days later in good condition. The drive comes in a very nice small box, with a perforated security seal to prevent tampering.
Arrival
We opened it up, followed the instructions (see “Installation” below) and used the drive for one week on a mixture of OS-X, Windows XP, Windows 7, and Linux. Our first impressions were disappointing, but over the course of the week, we found the Ironkey drive’s true strengths. As an “Authentication centric” reviewer, we focused on the password manager first, which in our opinion, is the most lackluster part of the whole package.
The IronKey’s true strength is hardware, encryption, and security minded tools. The hardware is nearly indestructible to normal abuse. You can wash it in industrial washing equipment, run over it with bulldozers, bake it in a 400 degree Fahrenheit oven, and do all sorts of nasty things to it and it will keep working. We’re not a hardware testing shop, so we didn’t try those things, but others have. Just look at YouTube.
Have some fun watching them. You’ll be amazed at the crazy things people have done to these drives and they keep working.
Installation
A small accordion style manual is included. Most of the manual lists features. Four pages are devoted to Windows, Mac (x86 only), and Linux setup. The guide refers users to “Dig Deeper” with the user guide pre-installed on the key. The included manual is very thorough and covers all aspects of the drive and software.
According to the printed manual, Ironkey supports Windows 2000, XP and Vista. The included User Guide PDF also specifies Windows 7 support.
We plugged the drive into a Windows 7, 64 bit system. Windows recognized the device as a CDROM drive and installed drivers without issue. As the instructions stated, we navigated to “My Computer” and drilled down into the Ironkey folder. If auto run is enabled, (Not recommended for security), the software will automatically run. We then clicked on the IronKey.exe setup file. The initialize screen appears.
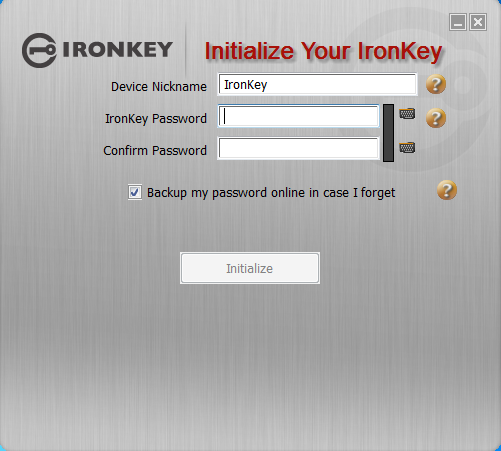
We typed our password. As you type, a little block turns from red to green when you have met the minimum four character requirement. We were disappointed to discover the password only had to be four characters. A proper strength meter would be more informative. Using the minimum four character password seems to defeat the purpose of buying a premium encrypted flash drive, but considering the drive will self-destruct after 10 failed login attempts, a four character password is probably sufficient. We still recommend at least eight. Using just four characters tempts people to use pin numbers and pin numbers may be found in your purse or wallet with your Ironkey.
Device Password Protection
The device password is hashed using salted SHA-256 before being transmitted to the IronKey Secure Flash Drive over a secure and unique USB channel. It is stored in an extremely inaccessible location in the is no “getPassword” function that can retrieve the hashed password), and only after the password is validated is the AES encryption key unlocked. The password try-counter is also implemented in hardware to prevent memory rewind attacks. All this ensures the ultimate protection for your data.
If you are running the setup on an untrustworthy or public machine, meaning you’re not sure if there may be keyloggers or malware installed, IronKey offers a virtual keyboard.
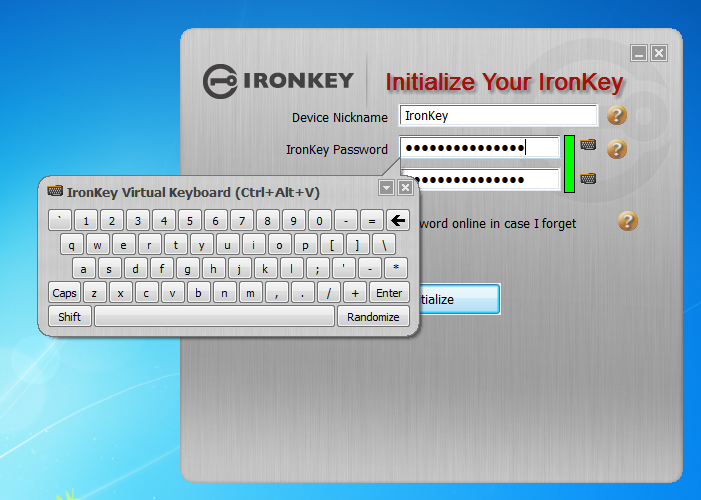
Some keyloggers take screenshots at each click, we expected the IronKey virtual keyboard to have a hover option to eliminate clicks, but it does not. Hover options enable you to float the mouse pointer over a key for x-seconds when the key will depress without clicking. Clicking on the small keyboard icon displays the Ironkey on-screen keyboard. This virtual keyboard offers a “Randomize” feature mixing the keys up so someone cannot watch from a distance easily. This made it very hard to find keys and will not help if screenshots are being taken as a hover option does.
Microsoft and Apple offer built in virtual keyboard with hover abilities. For Windows, you can run this simply by typing start/run then key enter osk and click run. If your run menu is hidden, you can search help and will find a reference. Mac users need to go into system configuration / Language then check "Keyboard viewer". Once that is done, a small US flag will appear in the menu bar. After clicking initialize a lengthy license agreement appears. After accepting the license agreement you are asked to activate the unit.

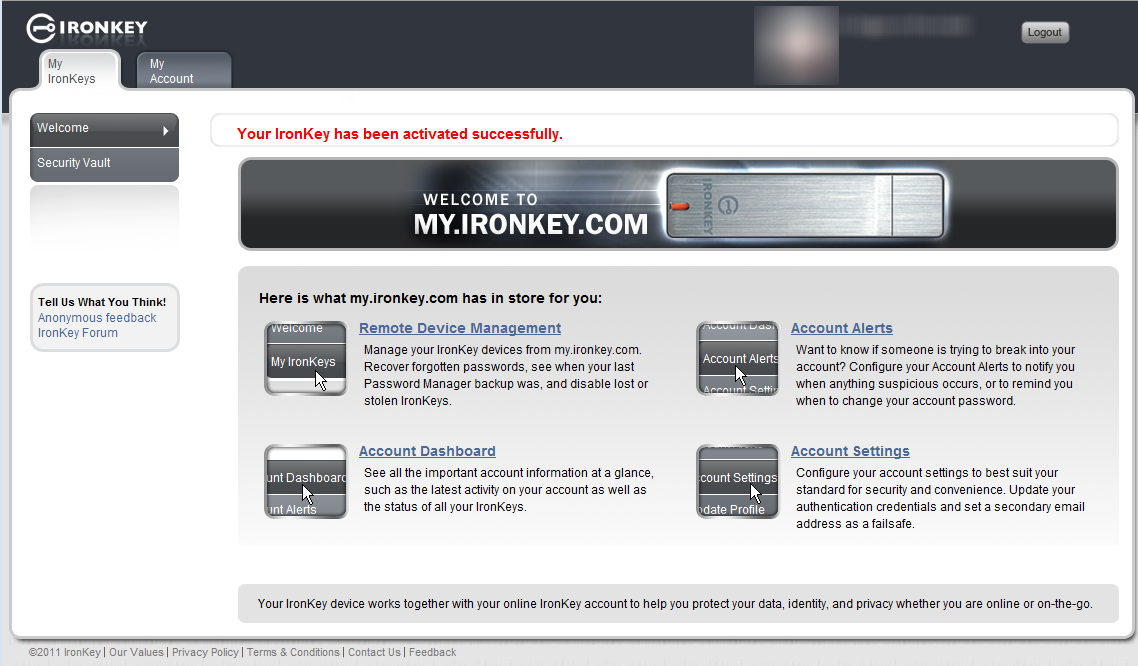
After activation, you are asked to setup an online account. If you choose yes, a portable copy of the Firefox browser runs from the IronKey and navigates to the IronKey registration pages. Firefox is a third-party browser, which is considered more secure than older versions of internet explorer. Registration involves providing a username, email, password (different than device), security photo, security questions, and security phrase (The phrase is included in emails to you to prevent phishing). An email is then sent to you with an activation code. After activation is complete, the browser will go to my.ironkey.com.
The software then installs Norton Safe Web Lite on the included Firefox browser running from the IronKey.
When you first insert the Ironkey into your USB drive on Windows, a new drive will be mapped to your system. This drive will look like a CD Drive titled “IronKey Unlocker”. The drive will be less than 100 megabytes. This is the read-only public / unencrypted part of the drive. To access the encrypted part, you will have to unlock it. For Windows or Mac, you simply run the IronKey application from the “IronKey Unlocker” and enter the password you setup when activating the key.
 Notice the option to unlock in read-only mode. If you are using the Ironkey and know you only need read-only access, check this off. It’s one extra step to prevent harm. After unlocking it, a new drive appears and the IronKey control panel displays.
Notice the option to unlock in read-only mode. If you are using the Ironkey and know you only need read-only access, check this off. It’s one extra step to prevent harm. After unlocking it, a new drive appears and the IronKey control panel displays.

The control panel only works under Windows and Mac. For Windows, you will see more applications than you will for Mac.
Ironkey Applications
FireFox and Secure Sessions
Using the included portable Firefox prevents your cookies, history, bookmarks, add-ons and memorized passwords from being stored on the local computer. Ironkey’s secure sessions is a secure privately run anonymous network. This type of service is called TOR. You can learn more about TOR at www.torproject.org. Essentially, when using a TOR browser, the traffic is encrypted to a secure IronKey server where it is decrypted and directed to the destination site. This slows things down a bit, but ensures that no-one can snoop on your browser traffic while on a public network such as free WIFI.
Note: a full service VPN is still more secure on the segment from your computer to the VPN service, but after that, TOR is more secure than VPN. The positive side of VPN is that it will encrypt all traffic (such as email client traffic), and not just the traffic from the browser.
To turn this on, you must click on the small IronKey icon at the bottom right hand side of the browser.
![]()
Ironkey includes a few nice utilities with the secure sessions program. You can access these by right-clicking on the task manager and selecting “Secure Sessions”.
Network Map
The network map shows which server is handling the secure tunnel visually showing the path. Here is a screenshot of a secure session to from our office to bing.
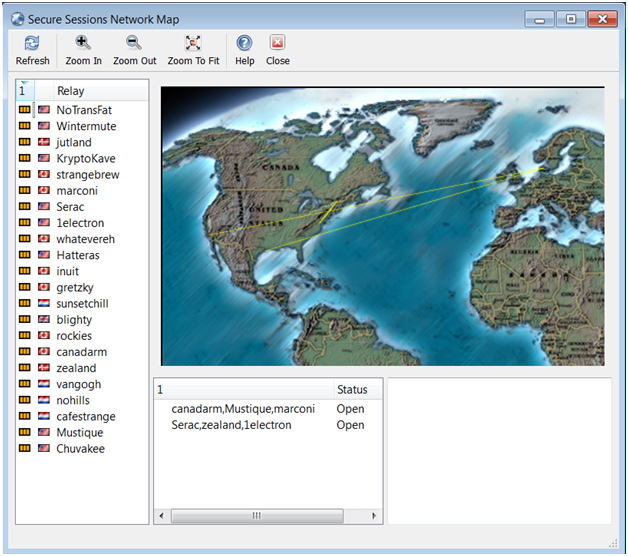
As you can see our path was from Pennsylvania to Washington State, but we bounced around the world on the way there. Another nice thing about the service is that it masks your source Address. We pulled a webpage from our own server and looked at the server access logs. It looked like we came from an unknown address rather than our own. When we trace the IP address from our own session it made it look like we were a user in Montreal Canada rather than from Pennsylvania.
Bandwidth Meter
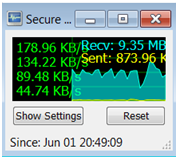
The bandwidth meter only shows traffic from the secure sessions. For an average user, this may provide no practical application, but it is interesting. We used a secure session to watch a youtube movie.
Our session stayed on the same path as the previous test. The youtube video we watched was a 360p resolution and we experienced no delays in playback at all.
Change Identity
The change identity button establishes new tunnels to different locations. We tried this then went back to our own site and looked at the log files. It now showed us having a source address from Washington DC instead of Canada.
My IronKey.Com
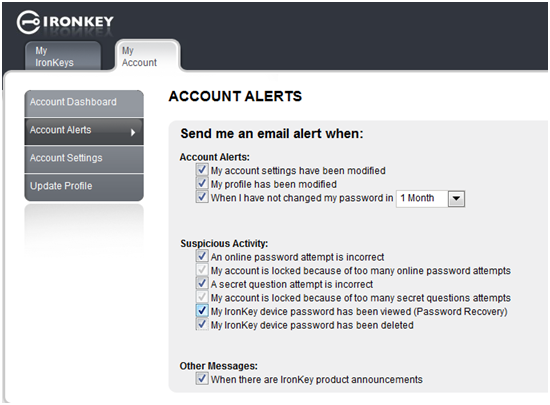
The included account at myIronkey.com provides the ability to recover a lost hardware password. Additionally you can set account alerts to inform you when someone is attempting to gain access to your account. You can get alerts for: Account modification, profile modification, changing password, online incorrect password attempt, locked account, failed secret question, password recovery, password deletion, and product announcements.
Identity Manager
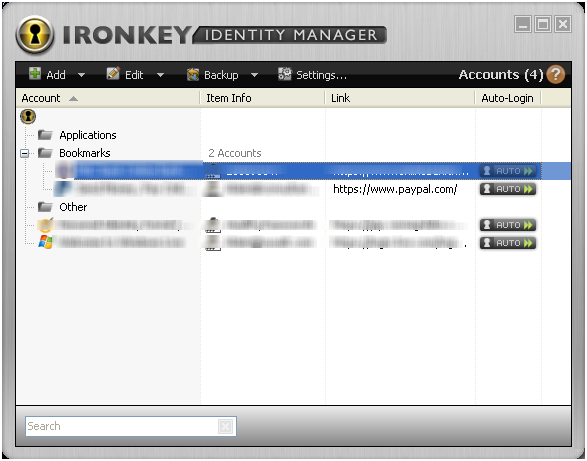
The identity manager is a very simple password manager. You add sites to the manager. Each site can contain the following information:
Username
Password
Link
Comments
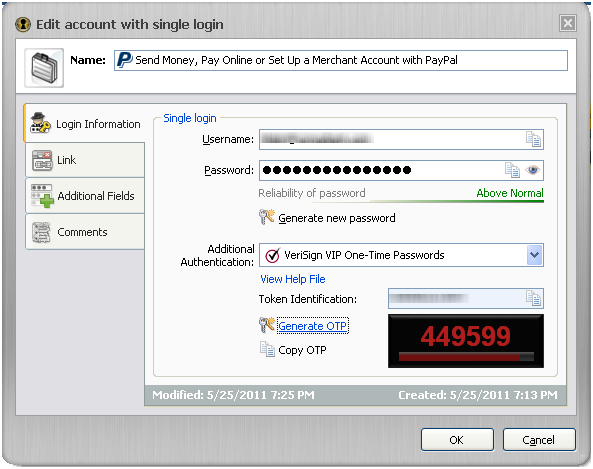
The username allowed up to 80 characters and the password field allowed up to 40 characters. Comments allowed up to 9322 characters.
An exciting feature of the Ironkey password manager is built in VIP credential support. VIP is a multi-factor authentication system by Verisign. To learn more about multi-factor authentication, see http://www.healthypasswords.com/content.Healthy_Passwords_What_is_Multi-Factor_Authentication.html/. Combining the VIP credential into the flash drive potentially eliminats a device from your keychain.
IronKey has tightly integrated the VIP functionality with the password manager. When you configure a site, you select “VeriSign VIP One-Time Passwords” under additional authentication.
We could not get IronKey single login with VIP working in the included portable Firefox for Paypal under Windows XP or Windows 7. In addition to portable Firefox a few browsers will show a new key icon at the top when the Ironkey is plugged in and unlocked. When using internet explorer 9 with the IronKey plugin, VIP with Paypal worked flawlessly.
When the drive is unplugged, the icon is removed.
Sites that used a simple username and password entry on the same form worked fine using the auto-login, but sites that use popup logins or split the login across two pages, such as sites that display a security ID after the username form is entered, did not work properly. We also found sites, like msn that don’t show a field, but instead show an icon that would not work properly until we clicked on the icon first.

In all these odd cases, you can use the copy to clipboard feature to paste the password. Identity Manager makes it easy to copy a password to the clipboard for pasting into forms. One nice feature is the Ironkey removes the clipboard entry after you have pasted it.
Identity Manager offers an online backup to your account vault. According to Ironkey, the datacenter holding the data is a secure facility in Virginia with armed guards and multiple circuits to the internet. Only your identity manager information is backed up. Files / Folders and settings are not backed up unless you backup locally through the separate backup utility.
Secure Backup
This feature backs up the contents of your IronKey drive to your local computer. Just specify a back up destination then click the back up now button.

The backup is placed in the same file structure as the drive. We first thought that the backup was unencrypted. To test it, we placed a text file named readme.txt on the drive. The file contained one line.
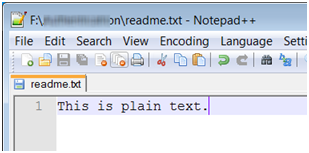
We then backed up the drive and opened the file from the backup location.
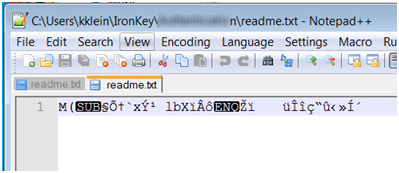
As you can see the file is no longer in plain text.
Another plus of the backup, is that it performs delta backups. This means that it is smart enough to only copy the files which have changed. Our first backup took a couple minutes and subsequent backups completed in seconds.
The utility backs up all files on the drive including system files such as the portable firefox and identity manager. These are stored in hidden folders under the destination folder.
Conclusion
We absolutely loved our week with the Ironkey. Other than our initial frustrations with the password manager, the copy password function was an acceptable work-around. The secure sessions alone is wonderful for public hot spots. If it saves five dollars a month on a VPN service, the drive pays for itself in a little over a year. The best part is if you lose it, you don't have to worry. If the finder is honest, they will plug it in and easily find your name, address and phone number displayed. If they are dishonest, they have 10 tries before it self-destructs (erases). Eighty-two dollars is a small price to pay for peace-of-mind.


|
Learn to Make Strong Memorable Passwords Today |

|
| ISBN: 978-0615456850 |
.
|
|
||
|
Home | Live CD Listing | Password Worksheet | Third Party Ratings | Purchase | Errata | Contact | News | News Archive | Legal Copyright © 2011, Sustainable Alternatives, LLC | Ligonier, PA 15658 | 724-238-9560 | All Rights Reserved. |

|
|
 |
.

